
The rise of blockchain technology and cryptocurrency has opened up a world of financial opportunities for individuals worldwide. However, this innovative space has also become a breeding ground for scammers looking to exploit unsuspecting victims. Whether you’re a seasoned crypto enthusiast or a newcomer exploring the market, it’s crucial to stay informed about the most common crypto scams and how to protect yourself. Here are eight prevalent scams to watch out for:
1. Wallet Draining Scams
Wallet drain scams are among the most devastating threats in the crypto world. Scammers trick victims into revealing their private keys or seed phrases, often by posing as legitimate entities or luring them to malicious websites. Once they gain access, they can transfer and drain your crypto assets in seconds.
How to Protect Yourself:
- Never share your private keys or seed phrases with anyone.
- Always verify that you’re on an official, trusted website—especially when using decentralized exchanges (DEXs).
- Use a hardware wallet for added security.
- Only download wallet apps or extensions from verified sources, and avoid fake ones.
2. Crypto Mining Schemes
Crypto mining scams come in various forms, but they all aim to steal your money or resources. Scammers may promise to double your investment with high-end mining rigs, sell you overpriced or fake hardware, or trick you into downloading malicious mining apps that hijack your device’s processing power (a practice known as cryptojacking).
How to Protect Yourself:
- Avoid offers that guarantee unrealistically high returns.
- Steer clear of mining apps, as they are rarely profitable and often malicious.
- Verify the credibility of hardware sellers before making a purchase.
3. Customer Support Impersonation Scams
Scammers often impersonate customer support representatives for wallets or exchanges, claiming to help with account issues, frozen funds, or lost passwords. Their goal is to trick you into revealing sensitive information like private keys or login credentials. These scams are common on social media and in the review sections of wallet apps.
How to Protect Yourself:
- Only contact support through official channels.
- Avoid clicking on links from suspicious accounts.
- Never share private keys or seed phrases—legitimate support teams will never ask for them.
4. Rug Pull Frauds
A rug pull occurs when developers of a new cryptocurrency project withdraw all the funds from the project’s liquidity pool, leaving investors with worthless tokens. These scams often involve bold promises about revolutionary technology to attract unsuspecting investors.
How to Protect Yourself:
- Verify that a token’s liquidity is locked using tools like Etherscan, BscScan, DexScreener, or RugCheck.
- Be cautious of newly launched projects with low market caps.
- Thoroughly research the development team and read independent reviews before investing.
5. Dusting Attack Tactics
In a dusting attack, scammers send tiny amounts of cryptocurrency (known as “dust”) to your wallet address. If you move these funds, they can track your transactions and attempt to de-anonymize you. This can lead to phishing, extortion, or other targeted attacks.
How to Protect Yourself:
- Avoid transferring unexpected small deposits to centralized exchanges or wallets holding large amounts.
- Use a crypto wallet with built-in protections against dusting attacks.
- Be cautious of unsolicited crypto transfers.
6. Pump-and-Dump Manipulation
Pump-and-dump schemes involve shady influencers or groups hyping up a low-value cryptocurrency (often meme coins) to artificially inflate its price. Once the price peaks, they sell off their holdings, causing the price to crash and leaving other investors with significant losses.
How to Protect Yourself:
- Avoid tokens with no solid fundamentals that are aggressively promoted on social media.
- Be wary of sudden price surges and low trading volumes relative to market cap.
- Conduct thorough research before investing in any cryptocurrency.
7. Hacked Accounts Luring Victims
Scammers often hack the social media accounts of influencers or well-known figures to promote fake crypto deals. They may promise to double your crypto, promote shady tokens, or offer fake airdrops that require connecting your wallet to malicious sites
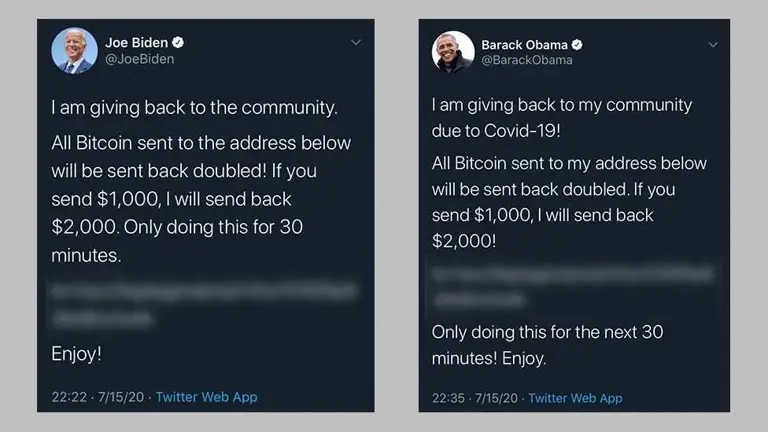
How to Protect Yourself:
- Verify through official channels if an account suddenly promotes a crypto deal.
- Remember that legitimate airdrops never require you to send money.
- Be skeptical of offers that seem too good to be true.
8. Pig Butchering Investment Scam
The pig butchering scam is a sophisticated romance scam where fraudsters build trust with victims through social media or dating apps before introducing a fake crypto investment opportunity. They may allow small withdrawals initially to build credibility, but once a large sum is invested, they block withdrawals and disappear with the funds.
How to Protect Yourself:
- Be cautious of anyone you meet online who pushes you toward crypto investments.
- Verify that any investment platform is legitimate and regulated.
- Never trust promises of guaranteed returns.
Final Thoughts: Stay Vigilant in the Crypto Space
The cryptocurrency space is a hotspot for scammers, and new tactics are constantly emerging. To protect your investments, always stay informed, conduct thorough research, and trust your instincts. If something sounds too good to be true, it probably is. By understanding these common scams and taking proactive measures, you can navigate the crypto world with greater confidence and security.
Remember, the best defense against scams is awareness and caution. Stay alert, be skeptical of unsolicited offers, and always prioritize the safety of your funds.





